Location
Introduction
Blockchain architecture is a groundbreaking way of organizing and securing digital information. At its heart, it’s like a digital ledger—imagine a diary shared across countless computers worldwide. Instead of one person keeping it, everyone gets a copy, and every new entry must be agreed upon by the group. This ensures that no single person can tamper with the data, making it trustworthy and transparent.
What sets blockchain apart is its clever structure: data is stored in “blocks,” and each block links to the one before it, forming a secure “chain.” This connection makes the system nearly impossible to alter, providing a solid foundation for applications like cryptocurrencies, secure contracts, and even tracking goods in supply chains. It’s a mix of teamwork, math, and technology that brings us closer to a more open and reliable digital world.
Breaking Down Blockchain Security with a Unique Interactive Visual
Blockchain is revolutionizing industries, but how secure are its foundations? Let’s dive into an engaging interactive visualization that explores the mechanics of consensus mechanisms, the potential vulnerabilities they face, and how these systems combat attacks. This article explains the visual step-by-step in an easy-to-understand manner, focusing on Proof of Work (PoW), Proof of Stake (PoS), and their Security Analysis, alongside an innovative attack simulation.
%%{init: { "themeVariables": { "nodeWidth": 180, "nodeHeight":250, "graphPadding": 30}}}%%
graph TD
%% Main Layers
A[P2P Network Layer] --> B[Consensus Layer]
B --> C[Smart Contract Layer]
C --> D[Data Layer]
A & B & C & D <--> E[Security Layer]
%% P2P Network Layer Components
A1[Node Discovery] & A2[Data Propagation] & A3[Network Sync] --> A
A1 --> |Peer List Exchange| A2
A2 --> |Block/Tx Broadcast| A3
%% Consensus Layer Components
B1[Proof of Work] & B2[Proof of Stake] & B3[BFT] & B4[DPoS] --> B
B1 --> |Block Validation| B2
B2 --> |Validator Selection| B3
B3 --> |Agreement| B4
%% Smart Contract Layer Components
C1[Virtual Machine] & C2[DApps] & C3[Token Standards] --> C
C1 --> |Execution| C2
C2 --> |Implementation| C3
%% Data Layer Components
D1[Block Structure] & D2[Storage] & D3[Merkle Trees] --> D
D1 --> |Chain Formation| D2
D2 --> |Verification| D3
%% Security Layer Components
E1[Cryptography] & E2[Key Management] & E3[Access Control] --> E
E1 --> |Encryption| E2
E2 --> |Authorization| E3
%% Layer Interactions
style A fill:#f9f,stroke:#333,stroke-width:4px
style B fill:#bbf,stroke:#333,stroke-width:4px
style C fill:#bfb,stroke:#333,stroke-width:4px
style D fill:#fbb,stroke:#333,stroke-width:4px
style E fill:#fbf,stroke:#333,stroke-width:4px
%% Component Styling
classDef component fill:#fff,stroke:#333,stroke-width:2px
class A1,A2,A3,B1,B2,B3,B4,C1,C2,C3,D1,D2,D3,E1,E2,E3 component
1. The Concept of Blockchain
A. Explanation of blockchain as a distributed ledger: This part clarifies that a blockchain is essentially a distributed ledger—a digital record that is maintained across a network of computers rather than stored on a central server. Each participant (node) on the network has access to the same version of the ledger, and updates or transactions are recorded across all nodes. This makes it harder to manipulate or alter the data.
B. Key characteristics: decentralization, transparency, and security: Here, the key features of blockchain are highlighted:
- Decentralization: The system is not controlled by a single authority, but rather by multiple participants (nodes), which reduces the risk of single-point failures or manipulations.
- Transparency: All participants have access to the same version of the blockchain, and transactions are publicly visible, providing a high degree of transparency.
- Security: Blockchain uses cryptographic techniques to secure the data, making it resistant to tampering or fraud. Each block in the chain is linked to the previous one, which adds a layer of security and makes it extremely difficult to alter past data.
2. Overview: Consensus Mechanisms in Blockchain
Consensus mechanisms are the backbone of blockchain networks, ensuring agreement among nodes and securing the system against tampering. This visualization highlights two popular methods:
A. Blockchain Architecture
At its core, blockchain is a distributed ledger technology where data is stored in blocks that are cryptographically linked. Here are the key architectural components:
- Nodes: Devices that maintain and validate the blockchain network. Nodes can be full nodes, which store the entire blockchain, or light nodes, which store only a portion.
- Blocks: Each block contains a list of transactions, a timestamp, and a reference to the previous block (hash).
- Consensus Mechanism: Ensures agreement on the blockchain’s state across all nodes, preventing tampering.
- Smart Contracts: Self-executing code that automates agreements and interactions on the blockchain.
This architecture creates a decentralized, secure, and transparent system that forms the foundation of blockchain applications.
B. Proof of Work (PoW)
- Visual Representation: A yellow-accented card representing mining processes.
- Key Features:
- Nonce Generation: A random number miners use to solve cryptographic puzzles.
- SHA-256 Algorithm: Ensures robust encryption.
- Dynamic Difficulty Adjustment: Keeps block creation time consistent (~10 minutes for Bitcoin).
Fun Fact: Bitcoin miners consume energy equivalent to small countries, but it’s all for maintaining network security!
C. Proof of Stake (PoS)
- Visual Representation: Green and blue accents reflecting validator selection and slashing mechanisms.
- Key Features:
- Validators are chosen based on their stake (e.g., 32 ETH for Ethereum).
- Misbehaving nodes are penalized via slashing, losing portions of their stake.
- More energy-efficient than PoW but requires strong economic deterrents to prevent malicious actions.
3. Security Analysis: Safeguarding the Network
Blockchain Consensus & Security Monitor
Network Status
Hash Rate
Block Height
Active Validators
Security Alerts
Potential 51% Attack Risk
Mining pool concentration above threshold
Network Latency Warning
Block propagation time increasing
Healthy Validator Distribution
Geographic distribution within parameters
Security in blockchain isn’t bulletproof. This section reveals common attack vectors and the defenses in place:
- Attack Vectors:
- 51% Attack: When a single entity controls the majority of network power.
- Sybil Attacks: Fake identities overwhelm the network.
- Eclipse Attacks: Isolating nodes from the network to manipulate them.
- Defense Mechanisms:
- Economic Penalties discourage malicious behavior.
- Checkpoint Systems validate critical blocks, preventing long-range attacks.
- Peer Reputation boosts trust among nodes.
4. Attack Simulation: Bringing Theory to Life
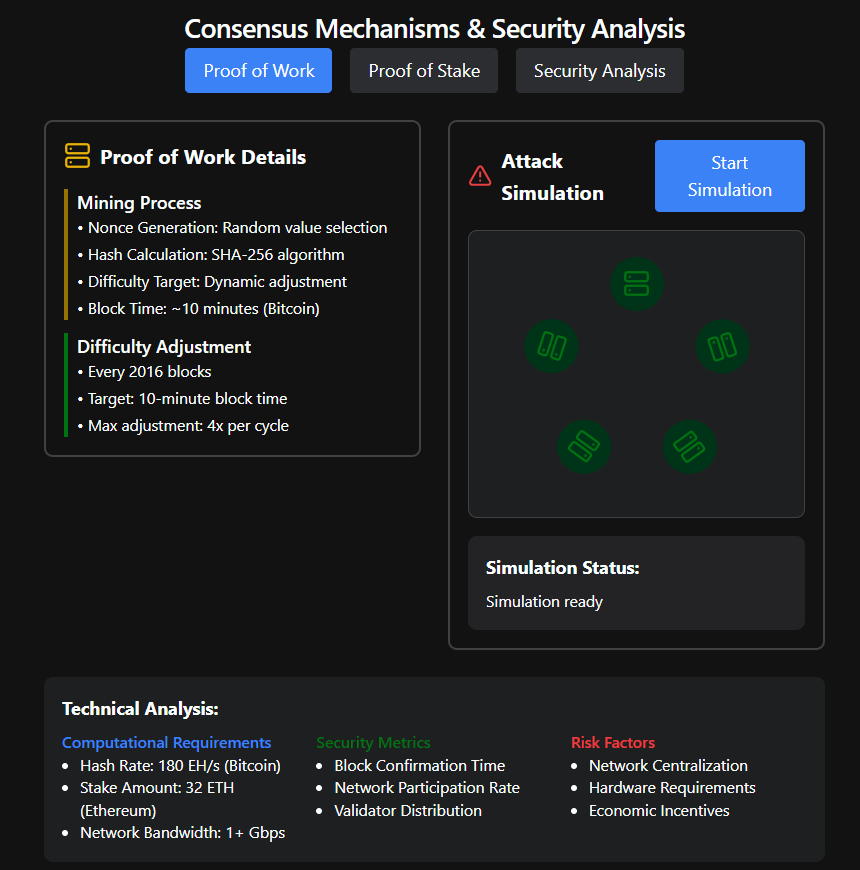
Here’s where the visualization shines—its interactive attack simulation lets users see blockchain vulnerabilities and defense mechanisms in action:
- Nodes Under Attack:
- Initially green (secure), nodes turn red one by one as the attack progresses.
- A pulsing red icon in the center dramatizes the ongoing breach.
- Simulation Status:
- Step-by-step updates narrate the attack process:
- Initiating malicious nodes…
- Attempting network isolation…
- Creating conflicting blocks…
- Propagating invalid chain…
- Attack detected – Prevention activated!
- Step-by-step updates narrate the attack process:
This interactive element is both educational and engaging, making blockchain security concepts accessible.
5. Technical Insights: The Numbers Behind the Systems
The visual concludes with a technical breakdown:
- Computational Requirements: PoW needs immense computational power (e.g., Bitcoin’s 180 EH/s), while PoS demands economic investment (e.g., Ethereum’s 32 ETH).
- Security Metrics: Focus on block confirmation times and validator distribution.
- Risk Factors: Centralization and economic incentives remain areas of concern.
Understanding blockchain architecture
Understanding blockchain architecture is essential because it forms the foundation for leveraging the full potential of blockchain technology across various industries. Here’s why it is important:
1. Efficient Problem-Solving
- A clear understanding of blockchain architecture helps in identifying whether blockchain is the right solution for a particular problem. It allows professionals to design systems that address specific challenges, such as transparency, trust, or decentralization.
2. Implementation and Development
- Knowledge of how blockchain works—its components, consensus mechanisms, and data structures—enables developers to build customized solutions. For example, understanding public versus private blockchains can help tailor the architecture to meet business or regulatory requirements.
3. Enhanced Security and Risk Management
- Blockchain architecture provides robust security mechanisms, but misconfigurations or poor design can introduce vulnerabilities. Familiarity with its structure helps in implementing strong cryptographic measures and minimizing risks like double-spending, hacking, or data breaches.
4. Scalability and Optimization
- By understanding the architecture, organizations can address common issues like scalability, transaction speed, and energy efficiency. This is crucial for deploying blockchain systems in high-demand environments, such as supply chains or financial services.
5. Interoperability
- Blockchain is often integrated with other technologies or systems. A thorough grasp of its architecture ensures seamless integration and facilitates communication between different blockchain networks or legacy systems.
6. Strategic Decision-Making
- Business leaders and stakeholders can make informed decisions about adopting blockchain, setting realistic goals, and managing resources effectively. This understanding helps align blockchain projects with organizational objectives.
7. Innovation and Research
- Understanding the underlying principles fosters innovation, enabling the exploration of new use cases or enhancements to existing blockchain platforms.
8. Regulatory Compliance
- Many industries must navigate strict regulations. Understanding blockchain architecture helps ensure compliance by designing systems that align with legal requirements regarding data privacy, record-keeping, and transparency.
In summary, comprehending blockchain architecture is vital for designing effective, secure, and scalable solutions, fostering innovation, and making informed decisions in both technical and business contexts.
Conclusion: Why This Matters
Blockchain’s promise lies in its decentralized and secure nature. Yet, understanding its inner workings is crucial for both enthusiasts and professionals. This visualization not only demystifies complex topics but also empowers users to appreciate the strengths and limitations of blockchain technologies.
Explore the visual for yourself, and see how blockchain defends against attackers in real-time!
FAQs
Here’s the updated version without white lines:
1. What is blockchain architecture, and how does it work?
Blockchain architecture refers to the underlying structure and design of blockchain technology. It consists of components like blocks, nodes, consensus mechanisms, and cryptographic security. Transactions are recorded in blocks, linked in a chain, and validated by a distributed network of nodes without a central authority.
2. What are the main components of blockchain architecture?
The key components include:
- Blocks: Containers of transaction data.
- Nodes: Participants in the network that validate and store data.
- Consensus Mechanisms: Protocols (e.g., Proof of Work, Proof of Stake) used to validate transactions.
- Smart Contracts: Self-executing code enabling automated agreements.
- Cryptography: Ensures data integrity and security.
3. What is the difference between public, private, and consortium blockchains?
- Public Blockchain: Open to anyone, with decentralized control (e.g., Bitcoin, Ethereum).
- Private Blockchain: Access is restricted to specific participants, offering more control (e.g., Hyperledger Fabric).
- Consortium Blockchain: Semi-decentralized, governed by a group of organizations rather than one entity.
4. How do consensus mechanisms impact blockchain architecture?
Consensus mechanisms define how transactions are validated and blocks are added. Common mechanisms include:
- Proof of Work (PoW): High security but energy-intensive.
- Proof of Stake (PoS): Energy-efficient but requires staking of cryptocurrency.
- Practical Byzantine Fault Tolerance (PBFT): Faster and suited for private blockchains.
5. What are the key challenges in blockchain architecture?
Challenges include:
- Scalability: Handling high transaction volumes.
- Energy Consumption: Especially in PoW-based systems.
- Interoperability: Connecting multiple blockchain networks.
- Latency: Delays in transaction confirmation.
- Regulatory Compliance: Adapting to legal frameworks.
6. How is data secured in blockchain architecture?
Blockchain uses cryptography to secure data:
- Hashing: Ensures data integrity by generating unique digital fingerprints for blocks.
- Digital Signatures: Verify the authenticity of transactions.
- Immutable Ledger: Prevents unauthorized data changes due to the linkage of blocks.
7. What are smart contracts, and how do they fit into blockchain architecture?
Smart contracts are self-executing programs stored on the blockchain that automatically enforce agreements when predefined conditions are met. They streamline processes, reduce manual intervention, and ensure transparency and trust in blockchain systems.




